Way of the Ronin
Software Composition Analysis (SCA): Finding & Fixing Vulnerabilities
Connecting Your GitHub to Aikido
Before diving into the security analysis, let’s first connect your GitHub account to Aikido so you can monitor your fork of DaBeastApp. Follow these steps:
👉 Log in to Aikido Security.
👉 Navigate to Integrations in the sidebar.
👉 Select GitHub and follow the instructions to authorize Aikido.
👉 Import your fork of DaBeastApp for monitoring.
For detailed instructions, check out Aikido’s documentation: How to Connect Your GitHub Account to Aikido.
Finding CVE-2022-29078 in Aikido
Once your repository is connected, Aikido will scan your dependencies. Navigate to Autofix in the Aikido dashboard and look for CVE-2022-29078 in the dependency report. This vulnerability is associated with a package used in DaBeastApp and can be exploited if left unpatched.
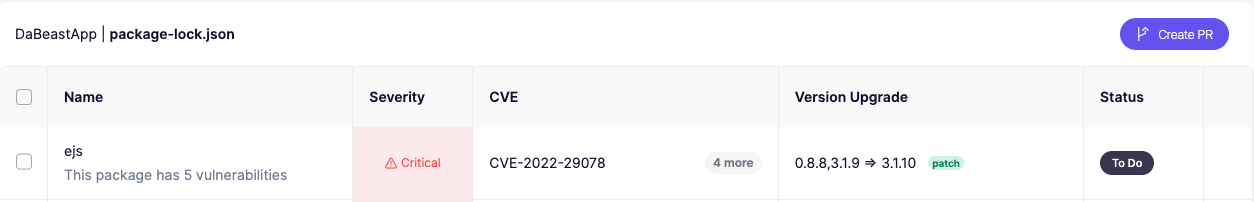
For an in-depth analysis, you can also navigate to Repositories > DaBeastApp where you can review additional context on found vulnerabilities including how you are using it in your code. Let’s check it out!
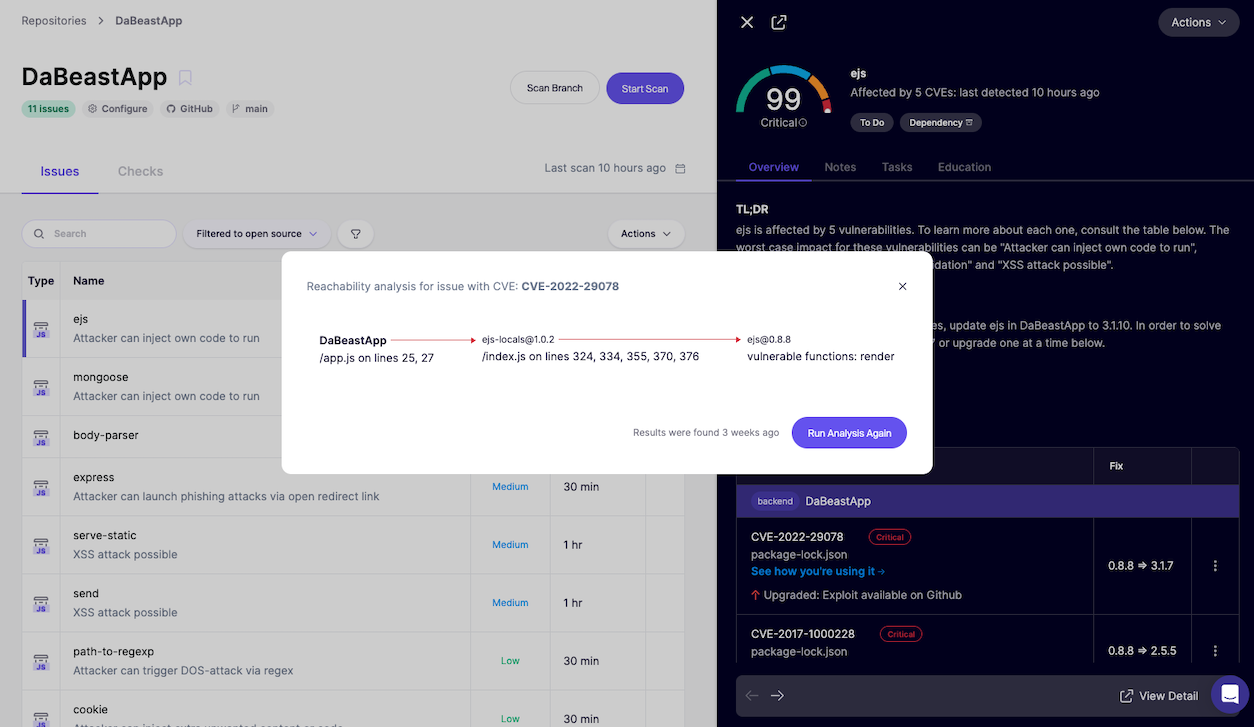
Understanding the Risk: How Attackers Exploit This Vulnerability
A vulnerability like CVE-2022-29078 can allow an attacker to inject and execute malicious scripts, manipulate data, or even gain access to sensitive user information. Similar vulnerabilities have been exploited in the past to conduct supply chain attacks, exfiltrate sensitive business data, and cause widespread service disruptions.
For example, the infamous Apache Log4j vulnerability led to mass exploitation across industries, affecting everything from cloud services to enterprise applications. Learn more about its impact from CISA’s guidance and this in-depth analysis.
Simulating an Attack: Why a WAF Might Not Save You
Let’s put ourselves in the mindset of an attacker and see how an exposed application could be compromised.
Try running the following HTTP request against your local instance of DaBeastApp:
curl -X POST http://localhost:3001/create \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "content=<script>alert('Hacked!')</script>"
This command sends a POST request to the app’s endpoint with a payload containing a script. If the app is vulnerable, the script will execute when a user views the task list.
What just happened? The application likely accepted the malicious input and stored it in the database. If a user loads the affected content, the script executes, leading to Cross-Site Scripting (XSS).
Now, you might be wondering, wouldn’t a Web Application Firewall (WAF) prevent this? The answer is: not always. Many WAFs rely on pattern-based detection and might fail to catch obfuscated or dynamically generated payloads. Attackers can also exploit business logic flaws that bypass WAF filtering entirely.
This is why defense-in-depth is crucial—relying solely on a WAF is not enough. We need to fix vulnerabilities at the source!
Checking the Database: Investigating the Attack
Let’s dig deeper and examine what’s happening at the database level. We want to see if our malicious payload made its way into the database.
First, open a shell session inside the MongoDB container:
docker exec -it dabeastapp-mongo mongosh
Next, switch to the application’s database and check for any suspicious records:
use express-todo
db.todos.find().pretty()
Do you see the malicious script stored in the database? If so, this confirms that the vulnerability is persistent, meaning it can impact multiple users who interact with the app.
This is a big deal. If this were a production environment, an attacker could steal session cookies, deface your UI, or even pivot to deeper exploits using stored XSS payloads. This technique can be used by attackers to persist malicious scripts in the database, potentially leading to widespread exploitation.
Fixing the Vulnerability with Aikido’s AutoFix
Aikido offers an AutoFix feature that suggests and applies security patches for open-source dependencies. Here’s how to use it:
- Go to your Aikido dashboard and navigate to Software Composition Analysis (SCA).
- Locate CVE-2022-29078 in the vulnerability list.
- Click AutoFix to generate a fix for the affected package.
- Review the proposed changes and apply them to your repository.
- Commit and push the changes to your feature branch.
For a more detailed guide, refer to Aikido’s AutoFix documentation: AutoFix for Open Source Dependencies.
Submitting Your Fix
Now that you’ve remediated the issue, let’s create a pull request (PR) to submit your fix.
- Go to your GitHub fork of DaBeastApp.
- Create a new Pull Request (PR) against the upstream repository (Tiger-Dojo/DaBeastApp).
- Add your GitHub username to the PR so we know who to give credit.
- Submit the PR and wait for review.
Once your PR is approved, you’ll receive credit for the lesson and earn an official Certifier badge for successful completion of this workshop!

Congratulations on grappling this lesson! 🚀 Let’s keep securing DaBeastApp!